Explain the Different Ways of Authentication
The passwords are of course hashed first and then stored in the database. Single-use PINs or pseudo-random numbers.

Authentication Vulnerabilities Web Security Academy
OTPs are another way to get access to the system for a single transaction.

. Authentication process can be described in two distinct phases - identification and actual authentication. According to all the information above and taking all the ways of authentication into consideration. Codes generated by the users smartphone Captcha.
Multi-factor authentication provides the following additional benefits. Multi-Factor Authentication MFA As the name suggests Multi-Factor Authentication involves at least two different kinds of authentication factors to elevate security levels. Common biometric authentication methods include fingerprint identification voice recognition retinal and iris scans and face scanning and recognition.
As security components are layered the complexity also rises. Fingerprints and handprints are the most widely used biometric method in use today. There are three basic types of authentication that we typically consider.
Multi-Factor Authentication MFA is an authentication method that requires two or more. Each of these. These user credentials are stored in the SQL Server database.
User authentication is the process of verifying the identity of user when that user logs into a computer system. Time-based One-time Password Algorithm based on the current time HMAC-based One-time Password Algorithm based on a counter. The modes of authentication are.
The user must then input that second one-time. The second is property-based meaning you possess something like an access card key key fob or authorized device that only you should have. Different types of tokens used in multi-factor authentication are.
Manage the connection between the human user and the websites server computer. Biometrics is the something you are method of authentication in other words you are your own key. Approve or decline the authentication so the system can move to authorizing the user.
Ad Use ID Identity Document Verification To Meet KYC AML GDPR Compliance. 2FA requires a user to be identified in two or more different ways. A user enters the username and password then both the server and the client generates a one-time password.
In the same way SQL Server also authenticates their users by their credentials. The process is fairly simple. Users input their credentials on the websites login form.
Custom authentication needs installation of ISAPI filter in IIS. In simple words Authentication means a process of identifying a user or a person based on their username and password. A mix of letters numbers and special characters make for a strong password but these can still be hacked or stolen.
One of the most common are the text CAPTCHAS where you need to look at random combinations of letters and numbers in the picture determine it and finally enter the characters in the attached form. Mixed Mode Authentication Windows SQL Server Authentication. Passwords can be in the form.
Unlike Two-Factor Authentication that is limited to two factors only MFA use cases can involve three or more of them. The most frequent authentication method is usernames and passwords. Three categories in which someone may be authenticated are.
Difficult to spoof and impersonate. While many systems use a fingerprint or retinal scan as a user password systems that are serious about security often use a password and a biometric scan before unlocking the computer or device. Biometric methods provide the something you are factor of authentication.
Something the user knows something the user is and something the user has. Passwords are the most common methods of authentication. There are different types of authentication systems which are.
Usernames or passwords can be used to establish ones identity thus gaining access to the system. Some ways to authenticate ones identity are listed here. This was the first method of security that was developed.
On this authentication system the user has to enter the username and. SQL Server uses the following 2 types of authentication. Explain the ways of authentication techniques in ASPNET.
These methods are used in applications that leverage two-factor authentication. The Extensible Authentication Protocol EAP Remote users can be authenticated via a Remote Authentication Dial-In User Service RADIUS or the Internet Authentication Service IAS. Fight Fraud Onboard Customers Faster With Jumios AI-Powered Identity Verification.
Biometrics should be cheap and reliable which should be universal permanent distinguishing reliable robust. The first is knowledge-based you know something like a password or PIN code that only you the identified user would know. 5 Common Authentication Types 1.
The main force behind. Apps that generate security codes via the third party thus enabling access for the user. Selection of an authentication provider is done through the entries in the webconfig file for an application.
Using e-mail or SMS OTP as a second factor is accomplished by sending a second one-time use password to a registered e-mail address or cell phone. Identification phase provides a user identity to the security system. Therere different types of CAPTCHAS.
That information is then sent to the authentication. Some of the biometric methods that can be used are fingerprints hand geometry retinal or iris scans handwriting and voice analysis. This is the usual Forms-based authentication in which the user who visits the web site needs to create an account with his login name and password.
Difference Between Authentication And Authorization Difference Between

Authentication Vs Authorization Okta
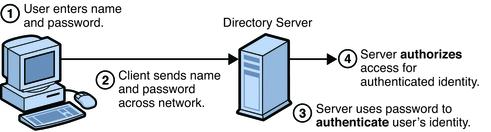
Password Based Authentication Sun Directory Server Enterprise Edition 7 0 Reference

Comments
Post a Comment